How to Configure Active Directory or LDAP Authentication Provider
Overview
NodeGrid supports the authentication and authorization of users through different authentication providers, like LDAP.
This guide will look at the different authentication options which are available with LDAP or AD Authentication
LDAP or Active Directory Authorization Provider
Nodegrid can be setup to authenticate users with LDAP or Active Directory servers. Nodegrid is using the LDAP protocol to do this. In order to setup a working authentication provider the following information are required.
| Field | Values | Required | Comment |
|---|---|---|---|
| Status | Enabled or Disabled | Yes | Default Value is Enabled. This means the provider will be used to authenticate users |
| Fallback if denied access | Enabled or Disabled | Yes | Default is Disabled. In this state if an authentication fails no other provider will be used to authenticate the user. It is recommended to Enable this feature in case the provider is not available |
| Remote Sever | FQDN or IP of LDAP server or domain | Yes | Nodegrid supports resolution of Active Directory Servers through DNS requests. This means that either specific Active Directory Servers can be specified or a valid Active Directory Domain. In case of the later the system will contact the closest Server based on the DNS results. |
| Base | Base DN | Yes | This field can contain the Root DN or a sublevel DN. This DN marks the highest point which will be used to search for users or groups |
| Secure | On, Off or Start_TLS | Yes | Default is off, all traffic between the Nodegrid and the LDAP server will be send unencrypted. Recommended On. Note this feature needs to be supported by the Server |
| Database Username | Search User Name | Optional | Full Qualified username, which can be used to search through the directory. Only required if the LDAP server requires authentication for browsing of the directory |
| Database Password and Confirm Password | Password for the search user | Optional | Only required if the LDAP server requires authentication for browsing of the directory |
| Login Attribute | Field which identifies the username | Required | |
| Group Attribute | Field which identifies the group names | Required | |
| Search Filter | Search Filter following the LDAP implementation | Optional | |
LDAP Servers
The LDAP protocol is an open standard and as such many commercial as well as open source products are available which implement this protocol. Due to this, there is a large variety of implementations, most of these will be similar but there are no clear standards for field names for example. All LDAP example in this document are based on an OpenLDAP implementation. One of the largest and widely used implementations of LDAP is Microsoft’s Active Directory. Sections which discuss Active Directory settings are specific to this implementation.
Microsoft Active Directory
Active Directory from Microsoft is a commercial product which is widely used in many companies. It allows companies to build up a very complex authentication provider implementation which reflects the internal organization of the company. An implementation can range from a single location/department to multi-site and global implementations. Due to this Active Directory servers can be grouped in Domains, which can be part of Tree’s which can be part of a Forest of different domains and Trees.
In order to find users in this structure a system can either interrogate a specific domain to which the user belongs or can interrogate the global catalogue, which lists all users and groups in the forest. It is important to note that even so the global catalogue list all the users and groups only the specific domains can successfully authenticate a specific user.
Nodegrid supports the interrogation of domain specific active directory servers as well as of global catalogue servers. Authentication of users is only possible against specific domains either by defining a specific Active Directory server or a specific domain in the configuration. In case multiple domains are required to be used for authentication, Nodegrid supports the configuration of multiple authentication providers. These can be arranged based preferred authentication provider list. The Nodegrid will then try to successfully authenticate the user against the various defined domains.
Value Overview and Samples
Status
The Status field enabled or disables the Authentication provider. The Provider will only be used in case the provider is enabled.
Fallback if Denied Access
The Fallback option allows user authentication with other providers in case the current provider is not available due to a network outage or the user authentication was rejected. This could be due to a valid authentication failure of the user or due to duplication of the user name in case multiple provider are available.
It is recommended to enable this option, as otherwise in case the provider is not available no authentication is possible.
Remote Server
This field is required. The IP address or the FQDN of the LDAP server are required. Only one IP or FQDN can be provided.
In order to provide failover options, multiple Providers can be created.
IPv4 Address Example:

IPv6 Address Example:

FQDN Example:

FQDN for an Active Directory Domain Example:

Base
The Base DN notes the highest point in the search structure for the authentication provider. Only elements like users and groups which are below this point will be searched.
The Base DN needs to be provided as a Distinguished Name. It has to be as minimum equal to the Root DN but it can be as well a sub DN
Base DN = Root DN Example:

Base DN = Sub DN Example:

Only users and Groups which are in or below the Marketing OU will be searched and authenticated
Secure
This field identifies the protocol which will be used to communicate with the Server. The default value of OFF is the normal LDAP protocol (TCP/UDP 389). This is an unsecured protocol and details like username and passwords are send in clear text to the authentication provider.
It is recommended to use the option ON this will use the SSL LDAP protocol TCP636, which will encrypt the traffic and ensures that username and passwords are not send in clear text. If required the TLS option is available as well.
NOTE: Support for SSL and TLS needs to be enabled on the Server. Specifically, AD servers do not support SSL or TSL by default.
Active Directory Kerberos is not supported at this point.
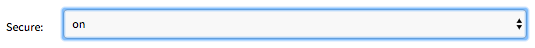
On Example:
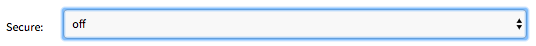
Off Example:
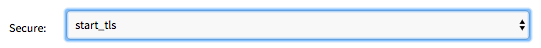
Start_TLS Example:
Database Username
This field is required in case the LDAP server requires authentication. This is the default setting for Active Directory servers for example.
The user name has to be provided as a Distinguished name. The search user can be outside of the provided base dn, but has to be a valid users. The base dn only applies to all search requests but not to the authorization of the search user.
NOTE: The scope of the user within the structure will have an impact on which users and groups can be searched. Ensure that the user is allowed to see all required groups and users in the LDAP or AD structure.
Example:
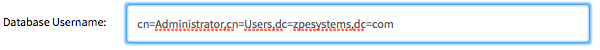
The field cn contains in most LDAP implementation the username. Different fields can be used as needed to identify the username. For Active Directory implementations, the cn field contains the username.
Login Attribute:
The Login Attribute is used to identify the field which contains the value with which the user identifies itself. This is typically the username. The value should identify user name values. In most LDAP implementations, this is by default the field cn (Common Name)
For Active Directory two values exist which can be used. It is a valid setup in Active Directory that both fields do not contain the same values. In case a login is not possible with a valid username it could be that this value is only maintained in one of the 2 fields within Active Directory.
| Field | LDAP Attribute |
|---|---|
| LDAP User logon | cn |
| AD User logon name | cn |
| AD User logon name (pre-Windows 2000) | sAMAccountName |
NOTE: Login through the Active Directory attribute userPrincipalName (username@domain.com) is currently not support.
LDAP Server Setup Example:
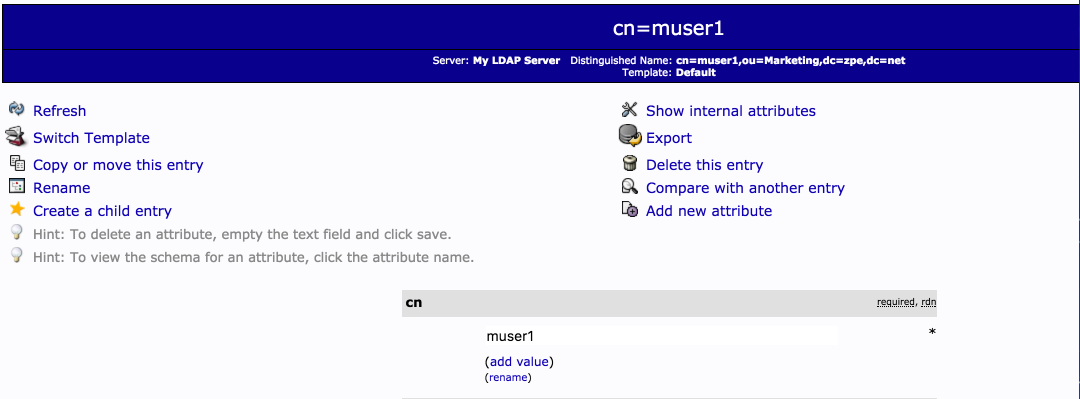
Login Attribute for a LDAP Server Example:

Login Attribute for Active Directory pre-Windows2000 User Name Example:

Login Attribute for Active Directory Windows User Name Example:

Member Attribute
The Member Attribute is used to identify which users are part of a group. The value should identify the field which contains the desired user name values. In LDAP servers, this is typically the memberUID field for Active Directory memberOf
| Field | LDAP Attribute |
|---|---|
| LDAP Member Attribute | memberUID |
| AD Member Attribute | memberOf |
LDAP Server Setup Example:
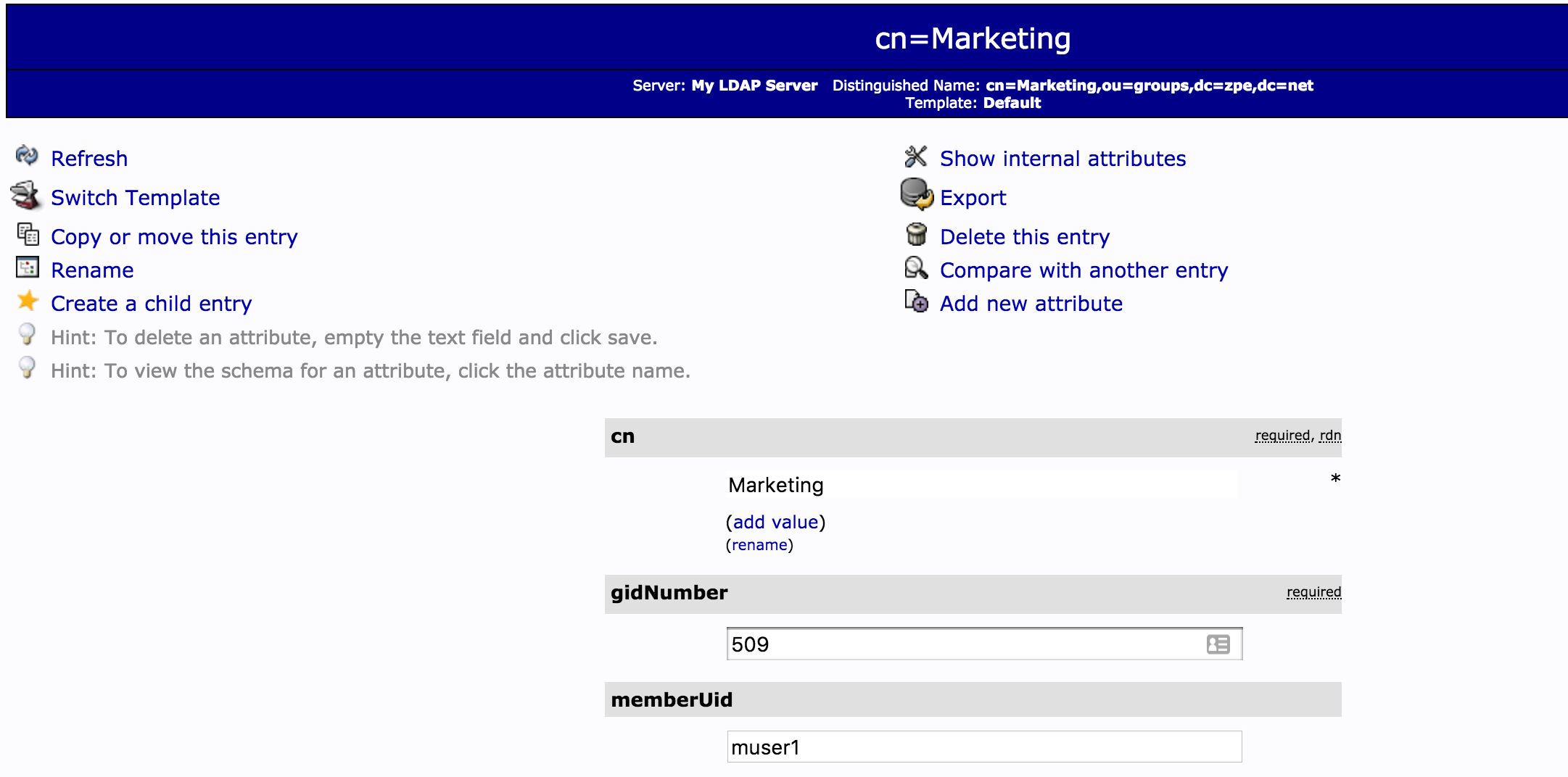
Member Attribute for a LDAP Server Example:

Member Attribute for a Active Directory Server Example:

Search Filter
The Search Filter provides an option to filter the search results based on the official LDAP search filter option. For example, could users be filtered out which have only a specific manager. The filter is applied after the base DN and search user’s limitations are applied
Configuration Examples
Login Attribute for a LDAP Server Example:

Login Attribute for Active Directory pre-Windows2000 User Name Example:

Login Attribute for Active Directory Windows User Name Example:

Setup of an LDAP Provider through the WebUI
- Login to the WebUI with an Administrator account
- Navigate to Security :: Authentication
- Click on the Add button
- Provide the following values (these are example values)
Field Value Comment Method LDAP or AD Status Enabled Fallback if denied access Active Remote Sever IP or FQDN of the LDAP Server Base dc=zpe,dc=net Secure OFF If a secure connection is supported by the server then it should be used Database Username cn=admin, dc=zpe,dc=net User will be used to search through the LDAP. This might not be required if anonymous browsing is enabled. Database Password and Confirm Password password Login Attribute cn Group Attribute memberUID Search Filter Not required - Example
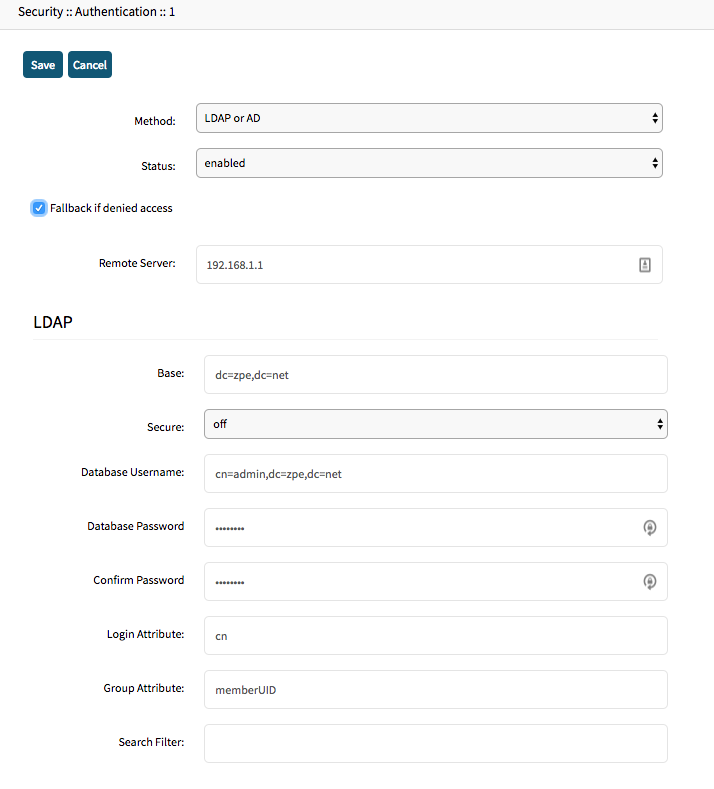
- Press 'Save' to save the authentication provider
Setup of an LDAP Provider through the CLI
- ssh to the Nodegrid with and administrator account
- Navigate to /settings/authentication/servers
- Start adding a new authentication provider with the command add
- Provide the following values (these are example values)
- These values can be provided as single values or as one set command.
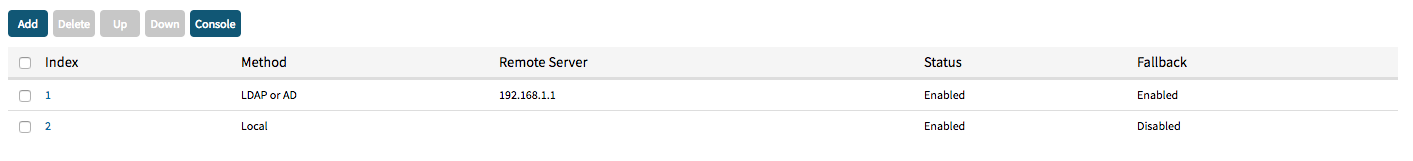
[admin@nodegrid {servers}]# set method=ldap_or_ad [admin@nodegrid {servers}]# set remote_server=192.168.1.1 [admin@nodegrid {servers}]# set fallback_if_denied_access=yes [admin@nodegrid {servers}]# set ldap_ad_secure=off [admin@nodegrid {servers}]# set ldap_ad_base=dc=zpe,dc=net [admin@nodegrid {servers}]# set ldap_ad_database_username=cn=admin,dc=zpe,dc=net [admin@nodegrid {servers}]# set ldap_ad_database_password=password [admin@nodegrid {servers}]# set ldap_ad_login_attribute=cn [admin@nodegrid {servers}]# set ldap_ad_group_attribute=memeberUID [admin@nodegrid {servers}]# commit - Commit the changes.
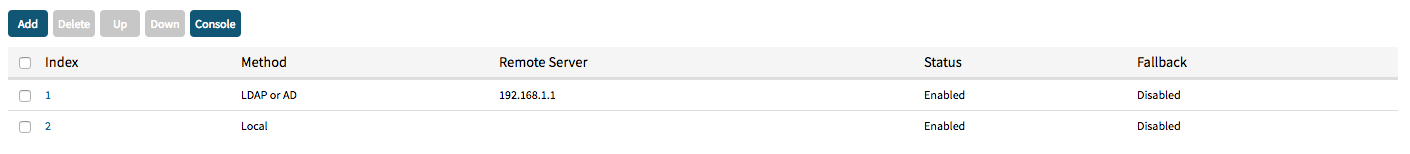
- To review the newly created authentication provider the command show or show_settings.
[admin@nodegrid servers]# show index method remote server status fallback ===== ========== ============= ======= ======== 1 ldap or ad 192.168.1.1 enabled enabled 2 local enabled disabled Try ls command instead... [admin@nodegrid servers]# show_settings /settings/authentication/servers/1 method=ldap_or_ad /settings/authentication/servers/1 status=enabled /settings/authentication/servers/1 fallback_if_denied_access=yes /settings/authentication/servers/1 remote_server=192.168.1.1 /settings/authentication/servers/1 ldap_ad_base=dc=zpe,dc=net /settings/authentication/servers/1 ldap_ad_secure=off /settings/authentication/servers/1 ldap_ad_database_username=cn=admin,dc=zpe,dc=net /settings/authentication/servers/1 ldap_ad_database_password=******** /settings/authentication/servers/1 ldap_ad_login_attribute=cn /settings/authentication/servers/1 ldap_ad_group_attribute=memeberUID
[admin@nodegrid servers]# add
[admin@nodegrid {servers}]#
| Field | Value | Comment |
|---|---|---|
| method | LDAP or AD | |
| remote_server | Enabled | |
| fallback_if_denied_access | Active | |
| remote_server | IP or FQDN of the LDAP Server | |
| ldap_ad_base | dc=zpe,dc=net | |
| ldap_ad_secure | OFF | If a secure connection is supported by the server then it should be used |
| ldap_ad_database_username | cn=admin, dc=zpe,dc=net | User will be used to search through the LDAP. This might not be required if anonymous browsing is enabled. |
| ldap_ad_database_password | password | |
| ldap_ad_login_attribute | cn | |
| ldap_ad_group_attribute | memberUID | |
| Search Filter | Not required | |
Setup of an Active Directory Provider through the WebUI
- Login to the WebUI with an Administrator account
- Navigate to Security :: Authentication
- Click on the Add button
- Provide the following values (these are example values)
- Example
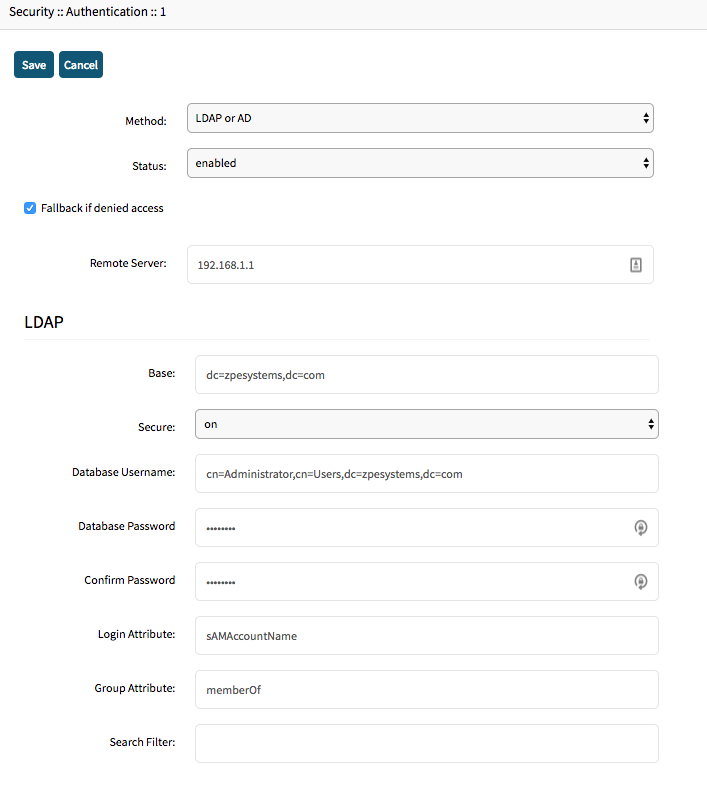
- Press "Save" to save the authentication provider
| Field | Value | Comment |
|---|---|---|
Method | LDAP or AD | |
Status | Enabled | |
Fallback if denied access | Active | |
Remote Sever | IP or FQDN of the AD Server | |
Base | dc=zpesystems,dc=com | |
Secure | OFF | If a secure connection is supported by the server then it should be used |
Database Username | cn=Administrator,cn=Users,dc=zpesystems,dc=com | User which will be used to search the Active Directory. This value should reflect the Distingueshed Name or the userPrincipalName |
Database Password and Confirm Password | password | |
Login Attribute | sAMAccountName | |
Group Attribute | memberOf | |
Search Filter | Not required | |
Setup of an Active Directory Provider through the CLI
- ssh to the Nodegride with and administrator account
- Navigate to /settings/authentication/servers
- Start adding a new authentication provider with the command add
[admin@nodegrid servers]# add [admin@nodegrid {servers}]# - Provide the following values (these are example values)
Field Value Comment method ldap_or_add remote_server 192.168.1.1 fallback_if_denied_access yes ldap_ad_base dc=zpesystems,dc=com ldap_ad_secure on If a secure connection is supported by the server then it should be used ldap_ad_database_username cn=Administrator,cn=Users,dc=zpesystems,dc=com User which will be used to search the Active Directory. This value should reflect the Distingueshed Name ldap_ad_database_password password ldap_ad_login_attribute sAMAccountName Correct values are either sAMAccountName or cn ldap_ad_group_attribute memberOf - These values can be provided as single values or as one set command
[admin@nodegrid {servers}]# set method=ldap_or_ad [admin@nodegrid {servers}]# set remote_server=192.168.1.1 [admin@nodegrid {servers}]# set fallback_if_denied_access=yes [admin@nodegrid {servers}]# set ldap_ad_secure=off [admin@nodegrid {servers}]# set ldap_ad_base=dc=zpesystems,dc=com [admin@nodegrid {servers}]# set ldap_ad_database_username=cn=Administrator,cn=Users,dc=zpesystems,dc=com [admin@nodegrid {servers}]# set ldap_ad_database_password=password [admin@nodegrid {servers}]# set ldap_ad_login_attribute= sAMAccountName [admin@nodegrid {servers}]# set ldap_ad_group_attribute=memeberOf [admin@nodegrid {servers}]# commit - Commit the changes
- To review the newly created authentication provider the command show or show_settings
[admin@nodegrid servers]# show index method remote server status fallback ===== ========== ============= ======= ======== 1 ldap or ad 192.168.1.1 enabled enabled 2 local enabled disabled Try ls command instead... [admin@nodegrid servers]# show_settings /settings/authentication/servers/1 method=ldap_or_ad /settings/authentication/servers/1 status=enabled /settings/authentication/servers/1 fallback_if_denied_access=yes /settings/authentication/servers/1 remote_server=192.168.1.1 /settings/authentication/servers/1 ldap_ad_base= dc=zpesystems,dc=com /settings/authentication/servers/1 ldap_ad_secure=off /settings/authentication/servers/1 ldap_ad_database_username=cn=Administrator,cn=Users,dc=zpesystems,dc= /settings/authentication/servers/1 ldap_ad_database_password=******** /settings/authentication/servers/1 ldap_ad_login_attribute= sAMAccountName /settings/authentication/servers/1 ldap_ad_group_attribute= memberOf
Setting Up User Permissions
After the authentication provider was added to the system, users will be able to be authenticated by the Nodegrid, but users are not yet authorized to access any resources on the Nodegrid.
For this remote user groups have to be assigned to appropriate internal groups. For this first create appropriate internal groups and assign the proper rights to them. After this was completed and verified you can assign remote groups to the internal Groups.
At this point end users can login to the Nodegrid and they will get the appropriate access to the system.
Individual users cannot be authorized by the Nodegrid, only user groups can be associated to internal groups.
Assign Remote Groups to Internal Groups WebUI
- Login the Nodegrid Manager with an admin account
- Navigate to Security :: Authorization
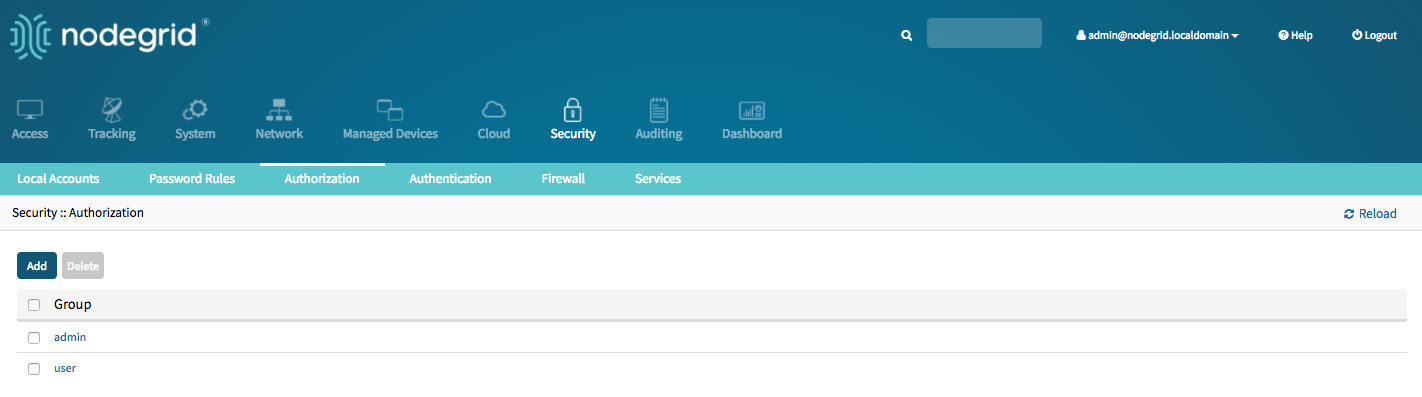
- Click on the Group to which the Remote Group should be associated with
- Go to Remote Groups
- Enter the group name and click on Save
- Multiple group names can be entered by separating them through a comma
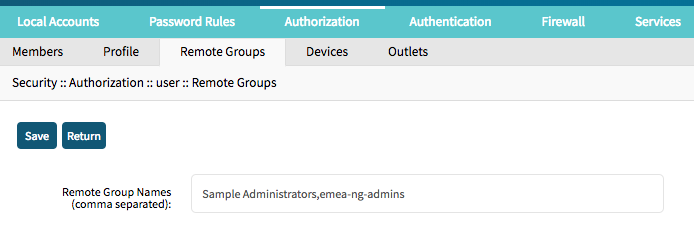
Assign Remote Groups to Internal Groups CLI
- ssh to the Nodegrid with an admin account
- navigate to /settings/authorization/
- navigate from here into the remote_group section of the group to which the remote group should be associated with
- use the set command to change the current setting and to associate the remote group
- multiple groups can be assigned by separating the group names with a comma
- commit the change
Example:
[admin@nodegrid /]# cd /settings/authorization/ [admin@nodegrid authorization]# show name ===== admin user Try ls command instead... [admin@nodegrid authorization]# cd admin [admin@nodegrid admin]# cd .. [admin@nodegrid authorization]# cd admin/remote_groups/ [admin@nodegrid remote_groups]# set remote_groups=emea-ng-admins [admin@nodegrid remote_groups]# commit [admin@nodegrid remote_groups]# show remote_groups = emea-ng-admins [admin@nodegrid remote_groups]# set remote_groups=emea-ng-admins,test [+admin@nodegrid remote_groups]# commit [admin@nodegrid remote_groups]# show remote_groups = emea-ng-admins,test
Appendix
Appendix A: Troubleshooting:
In case an authentication provider cannot be setup successfully, the following steps can be performed from the command line of the Nodegrid
- ssh to the Nodegrid as admin users
- navigate to the root shell
[admin@nodegrid /]# shell WARNING: Improper use of shell commands could lead to data loss, the deletion of important system files or other unexpected result. Please double-check your syntax when typing shell commands. admin@nodegrid:~$ sudo su -
Ping Authentication Provider with FQDN
root@nodegrid:~# ping zpesystems.com PING zpesystems.com (192.168.1.1): 56 data bytes 64 bytes from 192.168.1.1: seq=0 ttl=56 time=4.329 ms
Ping authentication provider with IP
root@nodegrid:~# ping 192.168.1.1 PING 192.168.1.1 (192.168.1.1): 56 data bytes 64 bytes from 192.168.1.1: seq=0 ttl=128 time=0.705 ms 64 bytes from 192.168.1.1: seq=1 ttl=128 time=0.724 ms 64 bytes from 192.168.1.1: seq=2 ttl=128 time=0.653 ms 64 bytes from 192.168.1.1: seq=3 ttl=128 time=0.564 ms
nslookup of Authentication provider
nslookup zpesystem.com Server: 127.0.0.1 Address 1: 127.0.0.1 nodegrid.localdomain Name: zpesystem.com Address 1: 192.168.1.1
ldapsearch against an Active Directory for an existing user:
root@nodegrid:~# ldapsearch -LLL -x -H ldap://192.168.1.1 -D 'Administrator@zpesystems.com' -W -b 'dc=zpesystems,dc=com' '(cn=Justin Wright)' Enter LDAP Password: dn: CN=Justin Wright,CN=Users,DC=zpesystems,DC=com objectClass: top objectClass: person objectClass: organizationalPerson objectClass: user cn: Justin Wright sn: Wright givenName: Justin distinguishedName: CN=Justin Wright,CN=Users,DC=zpesystems,DC=com instanceType: 4 whenCreated: 20180326195942.0Z whenChanged: 20180326200356.0Z displayName: Justin Wright uSNCreated: 520377 memberOf: CN=Sample Administrators,CN=Users,DC=zpesystems,DC=com uSNChanged: 520392 name: Justin Wright objectGUID:: 9FsZeFyyak+tScZRVyqPTw== userAccountControl: 66048 badPwdCount: 0 codePage: 0 countryCode: 0 badPasswordTime: 0 lastLogoff: 0 lastLogon: 0 pwdLastSet: 131665679826212339 primaryGroupID: 513 objectSid:: AQUAAAAAAAUVAAAAjw/uUGff8yuIeUgVfQQAAA== accountExpires: 9223372036854775807 logonCount: 0 sAMAccountName: jwright sAMAccountType: 805306368 userPrincipalName: justin.wright@zpesystems.com objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=zpesystems,DC=com dSCorePropagationData: 20180326195942.0Z dSCorePropagationData: 16010101000000.0Z lastLogonTimestamp: 131665682364029623 # refldap://ForestDnsZones.zpesystems.com/DC=ForestDnsZones,DC=zpesystems,DC=com # refldap://DomainDnsZones.zpesystems.com/DC=DomainDnsZones,DC=zpesystems,DC=com # refldap://zpesystems.com/CN=Configuration,DC=zpesystems,DC=com
ldapsearch against an Active Directory for an existing group:
root@nodegrid:~# ldapsearch -LLL -x -H ldap://192.168.1.1 -D 'Administrator@zpesystems.com' -W -b 'dc=zpesystems,dc=com' '(cn=Sample Administrators)' Enter LDAP Password: dn: CN=Sample Administrators,CN=Users,DC=zpesystems,DC=com objectClass: top objectClass: group cn: Sample Administrators member: CN=Justin Wright,CN=Users,DC=zpesystems,DC=com distinguishedName: CN=Sample Administrators,CN=Users,DC=zpesystems,DC=com instanceType: 4 whenCreated: 20180326200105.0Z whenChanged: 20180326200649.0Z uSNCreated: 520386 uSNChanged: 520395 name: Sample Administrators objectGUID:: F/BsFBsnVE+Sidvmc3M8YQ== objectSid:: AQUAAAAAAAUVAAAAjw/uUGff8yuIeUgVfgQAAA== sAMAccountName: Sample Administrators sAMAccountType: 268435456 groupType: -2147483646 objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=zpesystems,DC=com dSCorePropagationData: 16010101000000.0Z # refldap://ForestDnsZones.zpesystems.com/DC=ForestDnsZones,DC=zpesystems,DC=com # refldap://DomainDnsZones.zpesystems.com/DC=DomainDnsZones,DC=zpesystems,DC=com # refldap://zpesystems.com/CN=Configuration,DC=zpesystems,DC=com
ldapsearch against an OpenLDAP server for an existing user:
root@nodegrid:~# ldapsearch -LLL -x -H ldap://192.168.1.1 -W -D 'cn=Sample User,ou=users,dc=zpe,dc=net' -b 'dc=zpe,dc=net' 'cn= Sample User Enter LDAP Password: dn: cn= Sample User,ou=users,dc=zpe,dc=net givenName: Sample gidNumber: 501 homeDirectory: /home/users/sampleuser sn: User objectClass: inetOrgPerson objectClass: posixAccount objectClass: top uidNumber: 1015 uid: suser userPassword:: cn: Sample User cn: suser
ldapsearch with LDAPS connection
root@nodegrid:~# LDAPTLS_REQCERT=never ldapsearch -LLL -x -H ldaps://192.168.1.1:636 -D 'Administrator@zpesystems.com' -W -b 'dc=zpesystems,dc=com' '(cn=emea-ng-admins)' Enter LDAP Password: dn: CN=emea-ng-admins,OU=Ireland,OU=EMEA,DC=zpesystems,DC=com objectClass: top objectClass: group cn: emea-ng-admins member: CN= Sample User,OU=Ireland,OU=EMEA,DC=zpesystems,DC=com distinguishedName: CN=emea-ng-admins,OU=Ireland,OU=EMEA,DC=zpesystems,DC=com instanceType: 4 whenCreated: 20170731130317.0Z whenChanged: 20170731134503.0Z uSNCreated: 405624 uSNChanged: 405649 name: emea-ng-admins objectGUID:: xcFVSeQP2EWSx5JBY4iqmA== objectSid:: AQUAAAAAAAUVAAAAjw/uUGff8yuIeUgVegQAAA== sAMAccountName: emea-ng-admins sAMAccountType: 268435456 groupType: -2147483646 objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=zpesystems,DC=com dSCorePropagationData: 16010101000000.0Z # refldaps://ForestDnsZones.zpesystems.com/DC=ForestDnsZones,DC=zpesystems,DC=com # refldaps://DomainDnsZones.zpesystems.com/DC=DomainDnsZones,DC=zpesystems,DC=com # refldaps://zpesystems.com/CN=Configuration,DC=zpesystems,DC=com
ldapsearch with TLS_Start connection
root@nodegrid:~# LDAPTLS_REQCERT=never ldapsearch -LLL -x -Z -H ldap://192.168.1.1 -D 'Administrator@zpesystems.com' -W -b 'dc=zpesystems,dc=com' '(cn=emea-ng-admins)' Enter LDAP Password: dn: CN=emea-ng-admins,OU=Ireland,OU=EMEA,DC=zpesystems,DC=com objectClass: top objectClass: group cn: emea-ng-admins member: CN=Sample User,OU=Ireland,OU=EMEA,DC=zpesystems,DC=com distinguishedName: CN=emea-ng-admins,OU=Ireland,OU=EMEA,DC=zpesystems,DC=com instanceType: 4 whenCreated: 20170731130317.0Z whenChanged: 20170731134503.0Z uSNCreated: 405624 uSNChanged: 405649 name: emea-ng-admins objectGUID:: xcFVSeQP2EWSx5JBY4iqmA== objectSid:: AQUAAAAAAAUVAAAAjw/uUGff8yuIeUgVegQAAA== sAMAccountName: emea-ng-admins sAMAccountType: 268435456 groupType: -2147483646 objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=zpesystems,DC=com dSCorePropagationData: 16010101000000.0Z # refldap://ForestDnsZones.zpesystems.com/DC=ForestDnsZones,DC=zpesystems,DC=com # refldap://DomainDnsZones.zpesystems.com/DC=DomainDnsZones,DC=zpesystems,DC=com # refldap://zpesystems.com/CN=Configuration,DC=zpesystems,DC=com
To add a detailed output of the communication between client and server, ldapserach can use parameters -d -1. Note that this will create a very verbose output including induvidaul packages and certificate exchange details.
Example:
root@nodegrid:~# LDAPTLS_REQCERT=never ldapsearch -LLL -x -Z -H ldap://192.168.1.1 -D 'Administrator@zpesystems.com' -W -b 'dc=zpesystems,dc=com' '(cn=emea-ng-admins)' -d -1
Related Articles
LDAP Authorization and Authentication
LDAP is an open standard and there is a large variety of implementations all similar but barring slight variations. Nodegrid OS has an option that lets you define the devices a user has access to via user group authentication. Learn how to configure ...How to Configure Okta in Nodegrid
How to configure Single Sign-On authentication in Nodegrid using Okta This document will guide the configuration required in Nodegrid, and Okta. Nodegrid currently supports SP-Initiated SSO, and IdP-Initiated SSO. Create the Nodegrid Application ...How to configure Single Sign-On authentication in Nodegrid using Duo.
This document will guide the configuration required in Nodegrid, Duo Admin Panel, and Duo Access Gateway. Duo Access Gateway Setup 1. Install Duo Access Gateway on a server in your DMZ. Follow the instructions for deploying the server, configuring ...User Group Permissions
Nodegrid allows you to create users and groups, and set the appropriate permissions for them. For example, user John belongs to group system-test, and the this group will be able to configure Nodegrid, track system information, and terminate session. ...Setting up Remote Authentication methods in NodeGrid
Note: this configuration applies only to software version 3.2.x and later. With NodeGrid Software version 3.2.x, it is now possible to have multiple authentication methods. Use Case In some networks, there may have more than one authentication ...